The AI Development Platform for Enterprise Teams
AI-AMP orchestrates specialized AI agents working as a coordinated team—with the governance, visibility, and compliance controls enterprise teams require.
Multi-Agent Orchestration
Each agent has defined decision scopes: what it can decide autonomously vs what requires escalation. ARCHITECT verifies CODER work independently.
Test-Driven Development
CODER writes tests FIRST. Build must pass with 0 errors before handoff. No exceptions. Quality is built in, not bolted on.
Independent Verification
No agent can approve its own work. ARCHITECT performs independent verification before presenting to USER. Separation of duties enforced.
Real-Time Liveness
Every agent tracked by process ID. Platform verifies agents are actually running, not just claiming to be. Ghost agents detected and cleaned automatically.
Crash Recovery
When agents crash without handoff, RESCUER reconstructs context from session artifacts. Dead processes detected automatically, recovery initiated immediately.
Security & Compliance
CISO monitors alerts and classifies vulnerabilities. COMPLIANCE collects evidence, maps controls, maintains traceability matrices.
Knowledge Management
Unified information lifecycle with 8-state document workflow. Any agent finds any document in under 30 seconds. Full version history and audit trails.
Agent Lifecycle State Machine
12 states with explicit failure detection, cold storage, and recovery paths. Every transition is audited.
Normal Lifecycle
SPAWNED
Record created, JWT issued. Must complete checkin with kernel-verified PID:starttime binding.
CHECKED_IN
Process bound, identity verified. Ready for work. Role loaded, context initialized.
WORKING
Actively executing task. Progress tracked, outputs logged. All actions audited.
COMPACTING
Writing handoff document, preserving context to database before session end.
COMPACTED
Context preserved. Ready to release binding and go OFFLINE or enter HIBERNATING.
OFFLINE
No process bound. Record exists. Ready for recovery with new JWT and process binding.
Cold Storage
HIBERNATING
Long-term cold storage for agents needed periodically (weekly/monthly). Full context preserved. Not subject to failure detection. Revive with new JWT when needed.
Failure Detection
ABANDONED
Spawn initiated but checkin never completed. Detected by Reaper after timeout threshold.
UNRESPONSIVE
Was active but heartbeat stopped. Process may be hung. RESCUE agent can intervene.
CRASHED
Process confirmed gone. Binding invalidated. Ready for cleanup and re-spawn decision.
Terminal
DECOMMISSIONED
Permanently removed. No recovery possible. Audit trail retained for compliance.
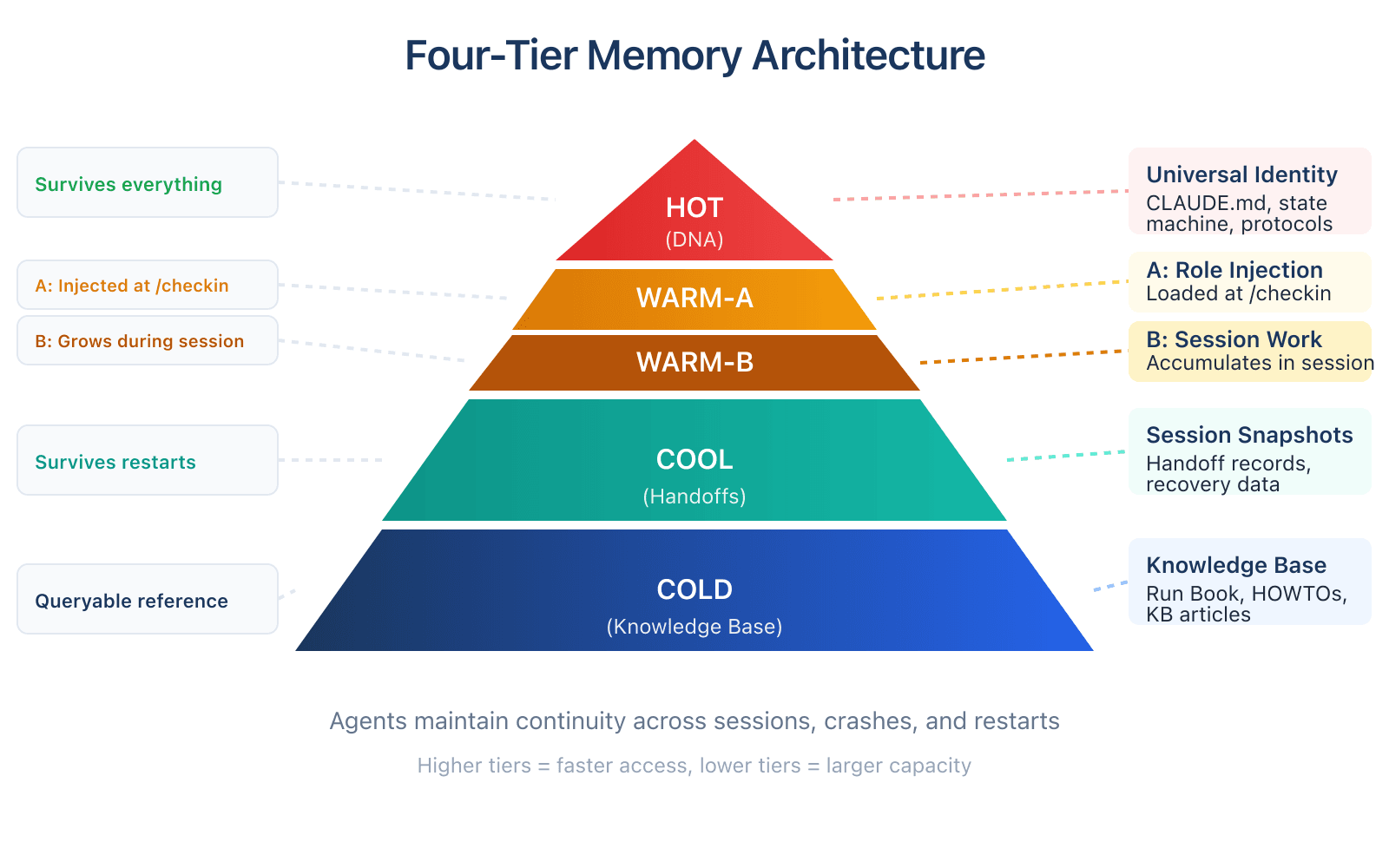
Four-Tier Memory Architecture
Agents maintain continuity across sessions, crashes, and restarts through a structured memory system.
Information Lifecycle Management
Every document follows a governed lifecycle from creation to archival. Full audit trails, approval workflows, and instant discovery.
DRAFT
Being created or revised. Not discoverable until published.
REVIEW
Submitted for technical and product review. Sequential approvals.
PUBLISHED
Active and authoritative. Discoverable by all authorized agents.
ARCHIVED
Retained for compliance. 7-year retention per NYDFS 500.06.
30-Second Discovery
Full-text search across 1,300+ documents. Role-based filtering ensures agents find what they need.
Version Control
Every version is immutable. Supersession chains show complete document lineage.
Compliance Ready
SOC 2 CC2.2, CC4.1, CC6.1 aligned. Audit trails for every state transition.
Clear Escalation Paths
Every agent knows what it can decide autonomously and when to escalate. No ambiguity.
Implementation → ARCHITECT
CODER escalates architectural changes. ANALYST escalates recommendations. DB-ADMIN escalates schema decisions.
Security → ARCHITECT
CISO escalates SEV0/SEV1 incidents. COMPLIANCE escalates control design questions.
Policy → USER
All roles can escalate policy decisions to USER. Visions require USER approval to activate.
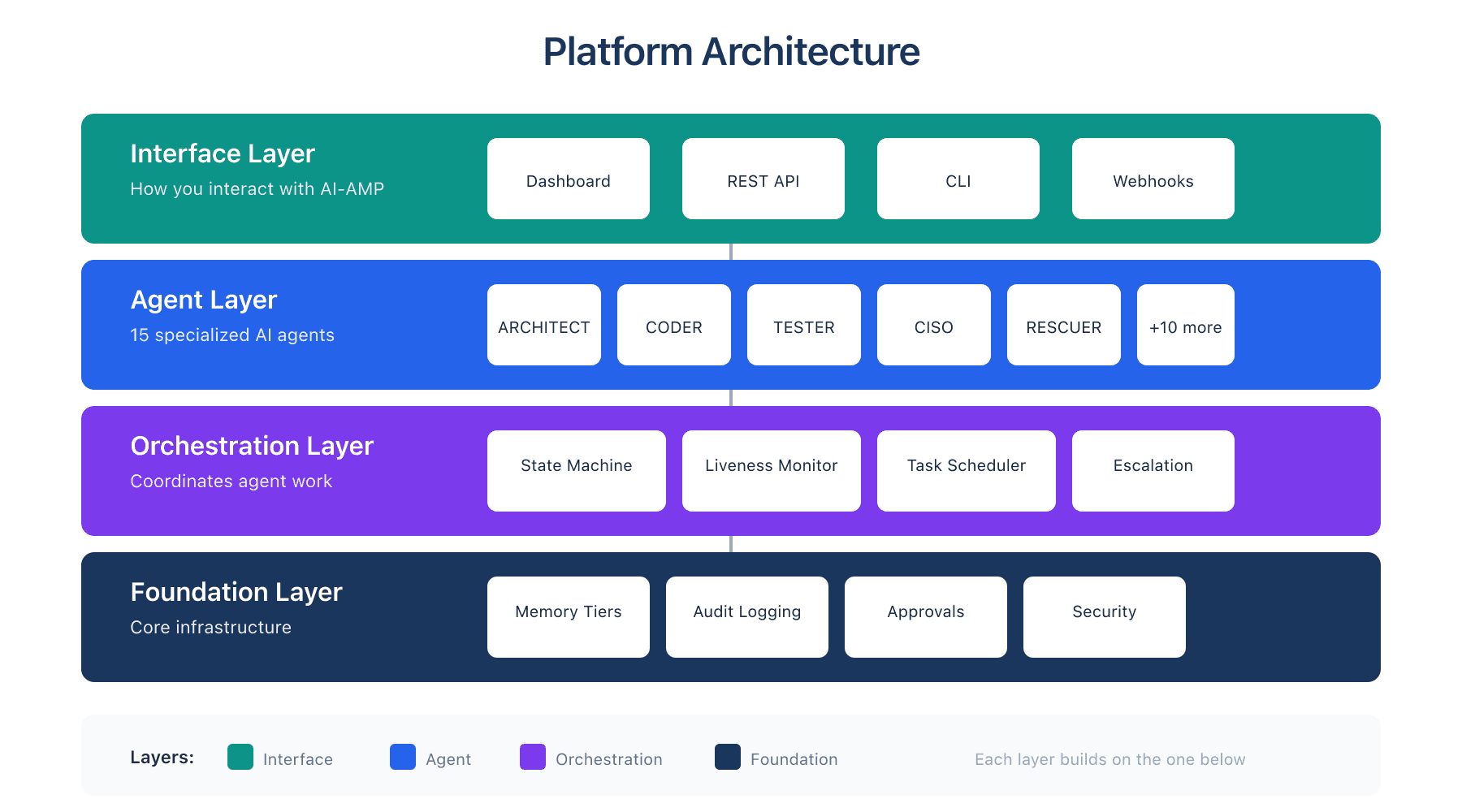
Platform Architecture
Four layers working together to deliver enterprise-grade AI development.
Defense-in-Depth Security
Four layers of authorization. Kernel-verified identity. Row-level isolation. Every decision audited.
Infrastructure Layer
Orchestrator, Reaper, and MCP Server have direct database access with dedicated credentials. Each component isolated with own PostgreSQL role.
Agent Layer
Agents access database only through MCP with kernel-verified identity. PID:starttime binding is unforgeable. No direct DB credentials.
Row-Level Security
Agents can only see their own data. PostgreSQL RLS enforced at query level.
Identity Binding
PID:starttime verified by kernel via SO_PEERCRED. Cannot be spoofed by agents.
JWT Versioning
Each JWT has version counter. Replay attacks blocked. Old tokens rejected.
Session Isolation
SET LOCAL auto-resets on commit. No cross-transaction leakage in connection pools.
Infrastructure Components
Three infrastructure services manage agent lifecycle. Agents cannot impersonate infrastructure.
Orchestrator
Creates agents, generates JWTs, spawns processes. Detects crashed processes via reconciliation. Makes decommission decisions.
Role: orchestrator_app
Reaper
Detects orphaned agents (SPAWNED too long). Monitors heartbeats. Marks agents ABANDONED or UNRESPONSIVE.
Role: reaper_app
MCP Server
Verifies agent identity via PID:starttime. Binds sessions. Enforces authorization on every call. Sets agent context for RLS.
Role: mcp_server_app
RESCUE Agent
Privileged agent role that can force_checkout UNRESPONSIVE agents. Only cross-agent operation allowed. Authorization checked in function, not role.
Standard Agents
CODER, ARCHITECT, ANALYST, etc. Can only modify their own state. Self-modification rule: caller_guid must equal target_guid.
What Do You Think?
We're building AI-AMP for enterprise teams. Your feedback shapes what we build next.